Categories
Archives
- September 2024
- August 2024
- July 2024
- June 2024
- April 2024
- March 2024
- January 2024
- December 2023
- October 2023
- September 2023
- August 2023
- July 2023
- May 2023
- April 2023
- February 2023
- January 2023
- November 2022
- October 2022
- September 2022
- July 2022
- May 2022
- April 2022
- February 2022
- January 2022
- December 2021
- November 2021
- September 2021
- August 2021
- July 2021
All storage accounts in Azure are encrypted by Storage Service Encryption (SSE) using a 256-bit Advanced Encryption Standard (AES) cipher. This makes Azure storage FIPS 140-2 compliant.
Important note
FIPS 140-2 is a US government security standard for the approval of cryptographic processes.
By default, the keys used to encrypt the storage are managed by Microsoft; however, there is also the option to use customer-managed keys instead. These keys can be provided by you or generated by Azure and stored in an Azure key vault. Some organizations demand that all data should be encrypted using individually managed keys.
Access to storage accounts also uses transport-level security in HTTPS to secure communications to the account. HTTPS connections are enforced by default; however, this can be disabled to allow HTTP if required.
Auditing
Auditing is another requirement for some organizations, especially for highly sensitive data. Breaches can happen. And even with well-defined security in place, a breach could occur from insider threats (for example, authorized users).
The Azure event logger logs control-plane events (for example when a storage account is created or deleted). Transactional logs can be activated and sent to an Azure Log Analytics account.
Azure Defender for Storage is another optional advanced threat protection service that can detect and alert unusual activity. Integrated into Azure Security Center, alerts can be sent via email to administrators with details of the event and advice on investigating and remediating.
Through a combination of network, authorization, and encryption, you can ensure your data is safe and secure. In the final section of this chapter, we will investigate the different tools available for managing the data in storage accounts.
Using storage management tools
You will need to copy data into and out of a storage account; therefore, we will examine the different tools available in this final section.
All data operations can be actioned by calling the Azure Storage REST APIs – in fact, all of the other tools that we will explore through this section use the REST APIs themselves.
Azure Storage REST APIs
Each storage service – Blob Storage, Data Lake, Files, Queues, and Tables – all have their endpoint URLs, as follows:
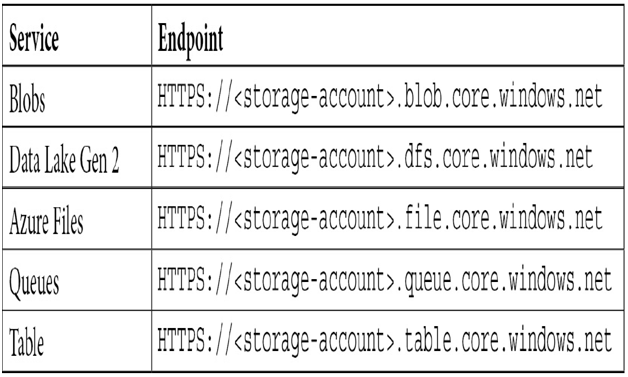
Each service, then, has its own unique set of calls that can be made depending on the action you are trying to take. For example, to get a list of all blobs within a folder, you can follow the GET call:
https://mystor.blob.core.windows.net/?comp=list&maxresults=3
Here, mystor is the name of the storage account. Note that if the storage account or container is set to private, you first need to make a call to the Azure authentication service to obtain an authorization token and then pass that token through to the REST endpoint header.
Although you could perform these actions manually, the REST APIs are meant for use programmatically.
Microsoft also provides several client libraries that you can use in your applications to make using them more manageable.
However, if you want to access it without writing your software, you can use the azcopy command.

Leave a Reply