Categories
Archives
- September 2024
- August 2024
- July 2024
- June 2024
- April 2024
- March 2024
- January 2024
- December 2023
- October 2023
- September 2023
- August 2023
- July 2023
- May 2023
- April 2023
- February 2023
- January 2023
- November 2022
- October 2022
- September 2022
- July 2022
- May 2022
- April 2022
- February 2022
- January 2022
- December 2021
- November 2021
- September 2021
- August 2021
- July 2021
Protecting your data is a crucial consideration with any storage mechanism. Luckily, security is at the heart of Azure components, and storage solutions implement various protection levels by default.
We will take a look at the different security options for Cosmos DB and Azure SQL in Chapter 12, Creating Saleable and Secure Databases. In this section, we will look at how to secure Azure Storage accounts.
Securing your data can be achieved in four different ways:
- Network protection: First, we need to protect your data against unauthorized access at the network level – only allow access from the applications that need access and no more.
- Authorization: Next, ensure that any system or person who can access the network level also has to access the data based on their account—in other words, use Role-Based Access Controls (RBAC).
- Encryption: Ensure data is encrypted so that if a hacker were able to bypass the network and role-based controls, they cannot access the data itself without access to the relevant encryption keys.
- Auditing and threat detection: If a breach does occur, auditing enables you to track down who, when, and how the data was accessed.
We will start with how to protect storage at the network level.
Network protection
The first step in access prevention is to stop applications or systems from accessing the data if they don’t need to. For example, an application might use a web interface to read and write the data – end users don’t need direct access. In this scenario, we should lock down access to the application itself.
By default, storage accounts allow access from all network devices, so anyone with the URL to a file in the storage account can access it. This is not required in the preceding example; instead, we can configure Azure storage to only allow traffic from a selected IP range or Azure subnet.
The following screenshot shows the Networking blade of a storage account configured to allow access from a set subnet:
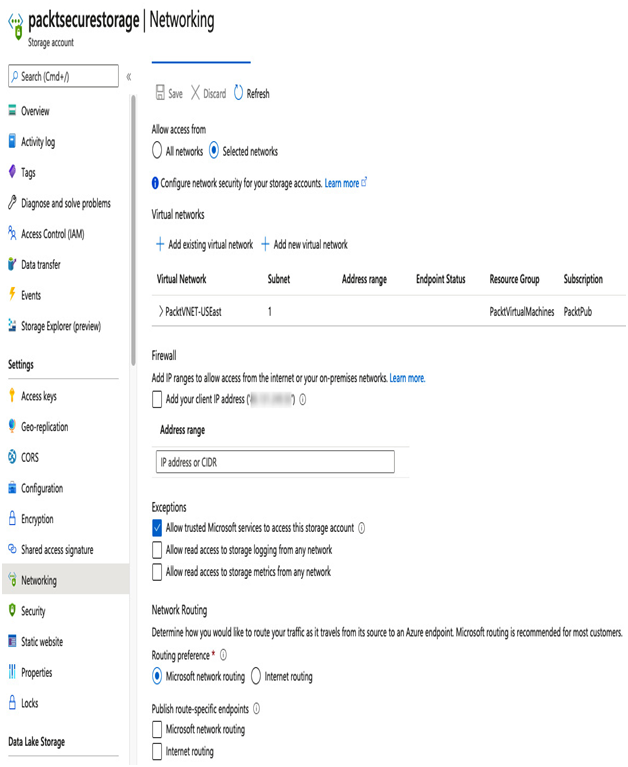
Figure 9.6 – Configuring storage network protection
Here, note the Exceptions section – by default, the option to Allow trusted Microsoft services to access this storage account is checked. This is useful because when you lock down a storage account, you might need to provide access to Azure Event Grid, Azure Data Factory, or a range of other Azure services. Although Microsoft does publish the IP ranges for these services, they are subject to change; therefore, checking this box opens the storage account to all of those services. Please refer to the following link for an up-to-date list of what is included: https://docs.microsoft.com/en-gb/azure/storage/common/storage-network-security.
Choosing whether to turn on network-level security requires some thought in terms of how your solution will work.
For example, a website might contain images and videos; however, these might all be stored in a storage account. To serve the media to end users, the web application can either get the files from the storage account and pass them to the user or supply a URL link to the asset directly in the storage account. In this situation, the account must be set to allow all networks, as the client could come from anywhere.

Leave a Reply